Federated Learning
What is federated learning?
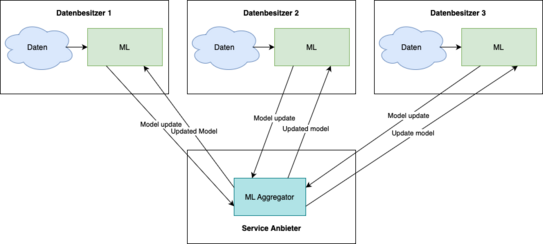
Without distributed machine learning, the data to be used for learning must be collected in one place to be shared. This poses high security risks and it is also not always possible to release all data. To still be able to learn with this data, distributed machine learning is applied. Instead of collecting data, each data owner has the machine learning model locally. The raw data does not leave the owner, but learning is done locally and only the resulting "model updates" are sent to a service provider. The service provider operates an ML aggregator, which aggregates the model updates and sends an updated model back to the data owners. This can be used to learn again locally on the data. This process is repeated until a termination criterion is reached.
What advantages does the approach deliver?
None of the data owners have to give out their data or collect it in one place. In addition, distributed learning is often more efficient because the data is already distributed and can be used immediately. In addition, the model for learning can be applied to smaller data sets.
Our current research topics
- Homomorphic encryption:
- Federated learning already creates some advantages in terms of data sovereignty and data security, but the "model updates" can still draw conclusions about the original data. Therefore, we extend the method with homomorphic encryption, which allows to work on encrypted data. The "model updates" are encrypted on the data owner's side before being sent and are then aggregated in the encrypted state and decrypted again only at the owner's side. To adapt the scheme to federated learning, we work with exciting techniques such as "Shamir Secret Sharing" to avoid having to use a single private key.
- Data Spaces:
- We also combine the approach with distributed and federated data spaces to apply the resulting benefits as well. In doing so, self-determination and thus data sovereignty is ensured above all. Each participant also becomes a participant in the data room through a connector and can determine for himself when and under what conditions his data is sent and used.
This is only a small insight. We are happy to welcome computer science students interested in these exciting research topics to our website. If you have further interest in our research or would like to learn more, please do not hesitate to contact us.